Using .gitlab-ci.yml to build, scan and store docker images on gitlab.com registry

Creating simple pipeline to build, scan and store your docker images on private gitlab.com registry
Do you know that you no longer need to use your private docker registry or Docker hub registry for image builds, vulnerability scans and etc? It’s been a while since I am using gitlab.com for all my pipelines, including image building, scanning for vulnerabilities and storing in private gitlab.com containers registry. It is very easy to setup, saves your time and allows automate tasks and moreover - is free (well with some limitations).
What you need to do is:
- Create private repository on gitlab.com
- Create .gitlab-ci.yml file (this file for your pipeline setup)
- In same repository create folder “builds” and subdirectory for your container image (like in my example: “builds/auth_srv”)
- Inside your container subdirectory add “Dockerfile” you wish to use for image build
Below is an example of pipeline file (all here to get you started). I won’t go into much details, as there is official gitlab.com documents already explaining in more details.
You don’t need to fill following variables as they are automatically filled by gitlab.com:
- $CI_REGISTRY_USER
- $CI_REGISTRY_PASSWORD
- $CI_REGISTRY
You will need to adjust repository paths as they should match your repository group, project name.
.gitlab-ci.yml example with clair image scanning
There is two stages:
- build -> Builds image
- scan -> Scans image and stores it into your gitlab.com private registry if no vulnerabilities detected.
Actual .gitlab-ci.yml file (adjust to your needs):
image: docker:19.03.1
services:
- docker:19.03.1-dind
stages:
- build
- scan
#-----------------#
# VARs #
#-----------------#
variables:
#---------------------------------------#
# VARs related to Docker runtime #
#---------------------------------------#
# -> Use TLS https://docs.gitlab.com/ee/ci/docker/using_docker_build.html#tls-enabled
DOCKER_HOST: tcp://docker:2376
DOCKER_TLS_CERTDIR: "/certs"
DOCKER_DRIVER: overlay2
#---------------------------------------#
# VARs related to images versions #
#---------------------------------------#
IMAGE_VERSION: "v0.04"
SCAN_ACCEPTANCE: "Medium"
services:
- docker:19.03.1-dind
#---------------------------------------#
# Script to run before builds #
#---------------------------------------#
before_script:
- docker login -u $CI_REGISTRY_USER -p $CI_REGISTRY_PASSWORD $CI_REGISTRY
- IMAGE_VERSION_DATE=$(date +%Y-%m-%d)
# --> auth_srv
build_image-auth_srv:
stage: build
only:
- master
script:
- docker version
- docker info
- docker build -t auth_srv:v$CI_COMMIT_SHORT_SHA builds/auth_srv
- docker tag auth_srv:v$CI_COMMIT_SHORT_SHA $CI_REGISTRY/devops/docker-images/auth_srv:latest-unverified
- docker push $CI_REGISTRY/devops/docker-images/auth_srv:latest-unverified
scan_image-auth_srv:
stage: scan
only:
- master
script:
- apk update && apk add coreutils
- docker network create scanning
- docker run -p 5432:5432 -d --net=scanning --name db arminc/clair-db:latest ; sleep 10
- docker run -p 6060:6060 --net=scanning --link db:postgres -d --name clair arminc/clair-local-scan:v2.1.0_8cb406fdb7ae7dc6fed05032b036a365391aaf42 ; sleep 10
- docker pull $CI_REGISTRY/devops/docker-images/auth_srv:latest-unverified
- docker run --net=scanning --rm --name=scanner --link=clair:clair -v '/var/run/docker.sock:/var/run/docker.sock' objectiflibre/clair-scanner --clair="http://clair:6060" --ip="scanner" -t $SCAN_ACCEPTANCE $CI_REGISTRY/devops/docker-images/auth_srv:latest-unverified
- docker tag $CI_REGISTRY/devops/docker-images/auth_srv:latest-unverified $CI_REGISTRY/devops/docker-images/auth_srv:latest
- docker push $CI_REGISTRY/devops/docker-images/auth_srv:latest
- docker tag $CI_REGISTRY/devops/docker-images/auth_srv:latest-unverified $CI_REGISTRY/devops/docker-images/auth_srv:$IMAGE_VERSION
- docker push $CI_REGISTRY/devops/docker-images/auth_srv:$IMAGE_VERSION
- docker tag $CI_REGISTRY/devops/docker-images/auth_srv:latest-unverified $CI_REGISTRY/devops/docker-images/auth_srv:$IMAGE_VERSION-$IMAGE_VERSION_DATE
- docker push $CI_REGISTRY/devops/docker-images/auth_srv:$IMAGE_VERSION-$IMAGE_VERSION_DATE
after_script:
- docker rm -vf db clair
- docker network rm scanning
You can trigger pipeline manually, via webhooks or via gitlab.com cron. Once triggered, jobs (stages) will be processed:
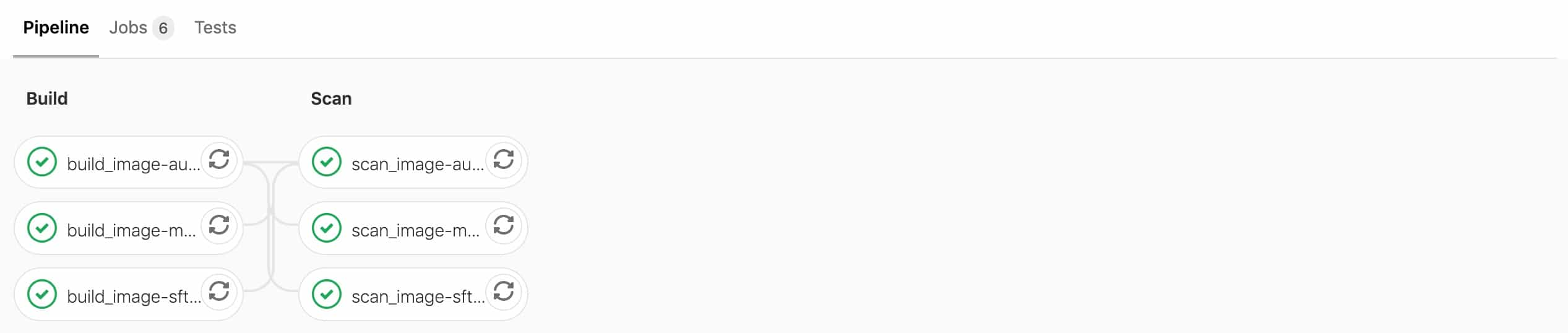
If all setup correctly, you should see following in CI/CD -> Pipelines -> Jobs:
You can expand this pipeline by including testing stage and etc.
I hope this helps!